The rising tide of client expectations for security and compliance is crushing MSP gross margins beneath tool sprawl and delivery complexity. To survive the future of managed services, MSP operators must stop confusing innovation with expensive software licenses. The only metric that matters for enterprise valuation is optimizing unit economics. I developed a framework, used when advising M&A roll-ups, to operationalize eight shifts based strictly on MTTR, gross margin, and scale. We start with how AI is fundamentally turning service delivery into a software model.
1. Architecting the AI-First Delivery Model
Linear service desk scaling drags down your unit economics. Every new client endpoint requires proportional headcount increases, capping gross margin potential and lowering M&A readiness. AI must resolve this fundamental constraint.
To maximize revenue outcomes, implement AI as a core service delivery shift, not a chatbot add-on. The engine handles routine, low-value work—ticket triage, summarization, SOP generation, and escalation routing. High-skill engineers shift exclusively to exceptions, ensuring every human resolution refines the system through specific, high-value input.
Start with bounded workflows: deploy AI for internal knowledge base (KB) search, “assist mode” response drafting, and automated ticket categorization. Crucially, establish a formal learning loop to compound system value. Assign ownership to a knowledge engineering function tasked with weekly AI error review, iterative KB updates, and explicit system feedback tagging. This refinement loop drastically reduces repetitive tickets per endpoint, cutting the delivery cost per client and unlocking predictable scaling without linear headcount growth.
2. Operationalizing Closed-Loop Automation for MTTR Reduction
If your Remote Monitoring and Management (RMM) platform only generates tickets for manual processing, you erode your unit economics. High-growth MSPs are shifting RMM value from passive monitoring to closed-loop remediation: an incident triggers a fix, not just an alert.
Predictive monitoring must couple with orchestration. The minimum viable architecture requires four components: reliable telemetry (for correct detection), standardized remediation runbooks (the defined fix), guardrails (approvals/rollback triggers), and exception handling.
Instead of automating everything, start with three high-volume, repeatable tasks that crush MTTR (Mean Time To Resolution) and lower ticket volume:
- Auto-restart failed services.
- Auto-isolate suspicious endpoint behavior (crucial for security).
- Auto-provision/replace failed virtual machines (where applicable).
This transformation shifts the scalability metric from linear headcount to endpoints per engineer. Reducing routine interruption frees high-skill personnel to focus on complex, strategic initiatives, thereby increasing profitability and client retention.
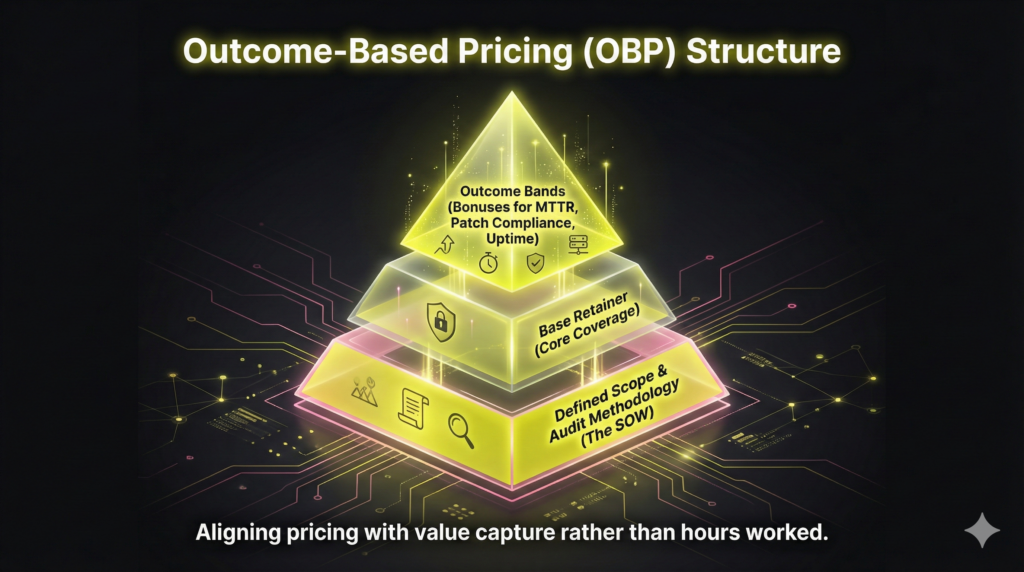
3. Shifting to Outcome-Based Pricing for Value Capture
Implementing AI-first delivery and closed-loop automation fundamentally shifts your unit economics toward efficiency. The strategic risk is clinging to per-hour or per-head pricing; this instantly devalues efficiency gains and commoditizes the automation designed to protect your margin.
The fix is transitioning to outcome-based pricing (OBP) to align incentives with the value of automated delivery. Structure contracts scalably: a fixed base retainer ensures coverage, supplemented by outcome bands tied directly to 2–4 measurable Service Level Agreements (SLAs).
Metrics must be auditable, client-impact focused, and allow for bonuses or penalties. Effective examples include MTTR (Mean Time To Resolution), Mean Time to Containment, patch compliance percentage, or uptime/availability. Crucially, define precise guardrails in the Statement of Work, outlining in-scope systems and the accepted measurement methodology. This prevents scope creep and is mandatory for maximizing long-term value capture.
4. Establishing the Managed Security Baseline for Value Capture
If your security offering is merely a periodic compliance checklist, you are already beneath the market’s new baseline. Modern boards and C-suite executives expect proactive security, detection, and auditable proof—not just promises. The MSP is now directly accountable for measurable detection, response, and continuous compliance posture. Clinging to legacy models ensures churn and competitive pressure.
The strategic solution is engineering security into a scalable, profitable managed security motion. This requires implementing two non-negotiable delivery components. First, adopt Zero Trust principles: strict identity verification, least privilege access, and micro-segmentation. Second, implement a formalized Managed Detection and Response (MDR) workflow that operationalizes the cycle: detect $\to$ investigate $\to$ contain.
Crucially, this operational rigor directly supports the outcome-based model. Continuous controls evidence and remediation tracking, facilitated by compliance automation platforms, transforms the quarterly audit nightmare into a repeatable, reportable service. This security-led packaging supports dramatically higher ARPU, reduces client switching risk, and solidifies value capture across the entire contract lifecycle.
5. Monetizing Multi-Cloud Sprawl via Unified Governance
The future of IT is fragmentation: multi-cloud sprawl, hybrid systems, and dozens of SaaS licenses are the standard operating model. This accumulation leads to unmanaged risk and unpredictable billing. If your MSP is still focused on individual vendor migration, you are missing the shift; clients now demand Unified Governance and cost control more than initial installation.
The strategic play is repositioning your value proposition from managing infrastructure to orchestrating risk and optimizing spend. Standardize an offering that delivers cross-cloud monitoring, identity/policy baselines, and crucial license optimization. This focus directly reduces tool sprawl and reactive remediation work, significantly improving your unit economics.
This governance-first sale is also easier to close. Prospects find “cost saved” and “risk reduced” instantly more tangible than technical administration. Furthermore, do not treat edge environments as separate silos; integrate them into the central governance and backup posture. Deliver visibility across the entire fragmented stack for predictable revenue outcomes.
6. Securing Automation ROI with Operational Change Management
Deploying advanced AI and closed-loop automation is useless if users bypass the system, making the investment a sunk cost. Automation requires Organizational Change Management (OCM) to secure ROI, prevent shadow IT, and maximize unit economics.
This is the true meaning of Shift-Left: moving resolution closer to the user via structured self-service assets. Competitors under-operationalize this layer, focusing solely on the portal technology. Your advantage is engineering the user experience with specific OCM deliverables: clear communication, role-based training, and mandatory onboarding checklists that guide clients toward the self-service portal as the first point of contact.
Focus on a “top 20 issues” deflection program. Integrating client-facing knowledge bases and guided workflows for your most frequent incidents dramatically increases your ticket deflection rate. This protects your margins without degrading the client experience. The KPI tie-in is direct: improved deflection rates and positive CSAT trends directly reduce the cost of delivery per endpoint, cementing operational rigor for maximized M&A readiness. (171 words)
7. Securing AI Deployment Through Mandatory Governance
Maximizing value capture requires that automation actions do not create uninsurable risk. When AI touches client environments, particularly within ticket resolution or security containment, oversight is no longer optional; it becomes a non-negotiable feature. An AI action implemented without governance creates immediate security gaps, privacy exposure, or catastrophic audit failures, jeopardizing relationships and lowering M&A readiness.
Standardizing AI Governance as a control layer is the strategic counter that justifies premium pricing. Implementation requires four governance essentials in every automation workflow:
- Role-Based Access Control (RBAC): Ensure AI executes only actions permitted by its assigned persona.
- Audit Trails: Mandate immutable logging of all AI-initiated actions for compliance and evidence retention.
- Client Data Boundaries: Explicitly define consent and boundaries for how AI processes client data.
- Drift Monitoring: Actively track when AI outputs degrade or produce unexpected results.
Enforce this rigor within your ITSM for automated approvals and in security operations for autonomous containment actions. Framing this technical rigor as risk management transforms a cost center into a core value differentiator that closes the sale.
8. Consolidating Your Tech Stack for Investor-Grade Platform Unification
Operating on a stack of 40 loosely integrated tools sacrifices unit economics and torpedoes M&A readiness. This tool sprawl creates hidden costs: fragmented data, duplicated technician effort, and inconsistent SLAs, directly undermining high-margin delivery models.
The modern MSP must evolve from a reseller of disparate software licenses to an integrator utilizing a coherent, unified platform. True platform unification requires clean integrations across core operations: PSA, RMM, ITSM, a tightly coupled security stack, and documentation/reporting tools. This operational rigor is the prerequisite for repeatable scaling.
Consolidation priorities must strictly focus on systems that drive measurable outcomes: (1) maximum automation coverage (reducing human touchpoints), (2) security response speed (cutting MTTR), and (3) reporting credibility (validating outcome-based contracts). Fewer tools and tighter integrations directly reduce service desk escalations and boost repeatability—a mandatory engineering decision for scaling without linear headcount increases.
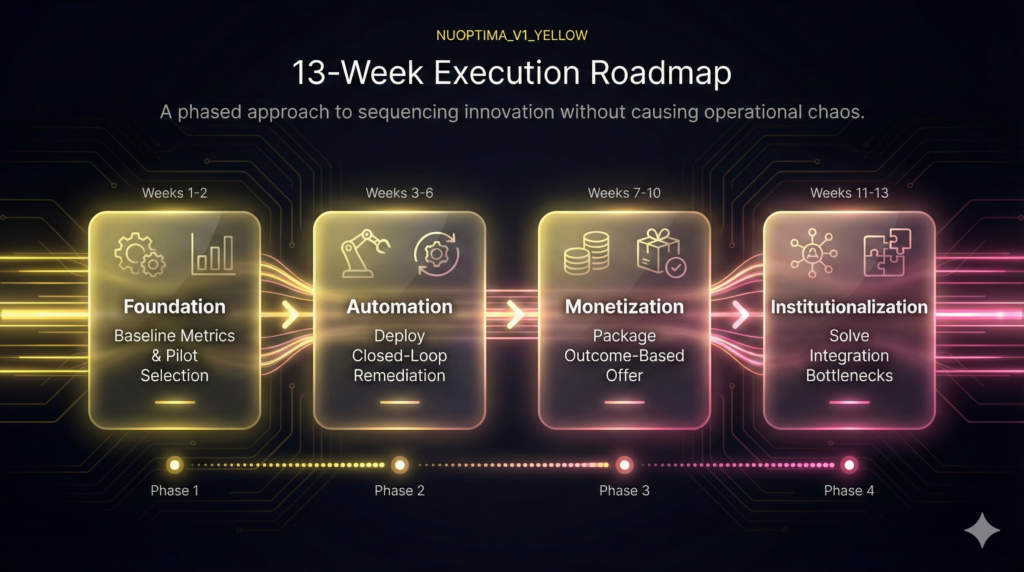
The 13-Week Execution Roadmap: Converting Trends to EBITDA
Adopting concurrent major technology shifts causes operational chaos and tool sprawl. Achieve compounding wins and maximize M&A readiness by sequencing innovation with a pilot-first approach. This 13-week schedule ensures automation investments deliver auditable improvements in unit economics and gross margin, securing investor-grade revenue outcomes.
Weeks 1–2: Establish the Pilot Foundation
Quantify the operational deficit. Select one service line for modernization: helpdesk deflection (using AI knowledge base search) or patch management/MDR.
- Baseline five key metrics: ticket volume, MTTR, escalations, CSAT, and client-level gross margin. This establishes the current state for clear ROI measurement.
- Identify two client accounts fitting your Ideal Customer Profile (ICP) for the pilot; secure their pre-pilot performance data.
Weeks 3–6: Implement Closed-Loop Automation
Achieve demonstrable MTTR reduction. Deploy one high-volume, high-repetition automation loop (e.g., auto-restart critical services).
- Standardize remediation runbooks for three common incidents.
- Enforce Audit Logging and RBAC (governance) to secure and document automated actions for compliance reporting.
Weeks 7–10: Package the Outcome-Based Offer
Monetize newfound efficiency. Formalize the automated service into a defined package detailing scope, expected outcomes, and reporting methodology.
- Pilot a hybrid pricing model on the 1–2 accounts.
- Use a fixed base retainer supplemented by outcome bands tied directly to measured metrics (MTTR or patch compliance percentage).
Weeks 11–13: Consolidate and Institutionalize
Institutionalize the new model. Address one critical integration bottleneck (e.g., where data breaks between the RMM/Security stack and the PSA).
- Integrate the automated service playbook into standard client Onboarding procedures.
- Mandate outcome metrics as the core focus of Quarterly Business Review (QBR) reporting to maximize repeatable delivery and reporting credibility.
Ready to diagnose where automation and outcome-based pricing will deliver the biggest immediate EBITDA impact? Request your custom Modern MSP Margin Audit today.
FAQ
Mitigate risk by combining a fixed base retainer with outcome bands tied to measurable KPIs, like Mean Time To Resolution (MTTR). Crucially, define precise scope boundaries in the Statement of Work. Include explicit exclusions for incidents caused by client policy violation, unsupported applications, or non-compliance. This prevents scope creep while maximizing value capture.
No, AI fundamentally shifts the required skill set, protecting technician utilization. While routine, low-value Level 1 work is highly automated, the demand grows exponentially for automation runbook engineering, knowledge curation, and governance. MSPs must plan for reskilling pathways that focus high-skill engineers on exceptions and strategic platform unification.
Closed-loop automation is mature enough, provided it is deployed incrementally and secured by governance. Start with “safe automations,” such as auto-restarting critical services or quarantining suspicious endpoints with an engineer approval loop. Always engineer clear rollback and override guardrails. Pilot these systems on a subset of endpoints before standardizing them across your entire client base.
Lead the sales conversation with auditable governance. Demonstrate that every AI action is secured by immutable audit trails, strict Role-Based Access Control (RBAC), and explicitly defined client data boundaries. Frame the technology as a superior risk management control, using continuous reporting to prove compliance and control outcomes. (See Section 7 above for governance essentials).
The only valuable strategic priority is one that strengthens your existing unit economics. Only integrate emerging domains (like edge computing or IoT management) if you can seamlessly govern, secure, and monitor them using your existing unified platform. Otherwise, any new silo of technology rapidly increases complexity and tool sprawl faster than it increases profitable revenue.