The closing dinner is not the finish line; it is the start of massive operational risk. The true threat to enterprise valuation is the post-close failure to capture technical and revenue synergies. Successful post-sale integration msp is a delivery-risk event demanding parallel execution across people, systems, and clients. This 100-day roadmap details nine practical moves MSP leaders must implement to stabilize the combined entityand protect the acquisition multiples paid for the business. Use this guide to identify your highest risk vector—people, systems, or clients—and act immediately to prevent client churn.
1. Establish a Single-Threaded Integration Management Office (IMO)
Erode deal value by allowing integration-by-committee, where decisions are bogged down by consensus. Successful post-sale integration MSP requires PE-style governance favored by top MSP consolidators: a high-velocity operating rhythm defined by clear accountability.
First, define the Integration Management Office (IMO) structure—this is the governance framework, not a new team. Appoint a single Integration Lead whose primary KPI is the successful completion of the 100-day plan. Under them, assign functional owners across Service Desk, Projects, Finance, Security, and Client Success.
Crucially, publish decision rights: document what functional owners can decide unilaterally versus what must be escalated to the Integration Lead.
Install the execution cadence: a tight, weekly standup focused solely on dependencies, staff risk, and client communication strategy. Measure execution success using a single, visible scoreboard tracking:
- Client churn risk list
- Staff retention risk list
- Service KPIs (SLA impact, MTTR)
- Financial KPIs (gross margin leakage)
Rule: If it is not on the scoreboard, it is not driving enterprise valuation. This focused, data-driven approach ensures execution velocity. (160 words)
2. Segment Key Personnel and Anchor Retention
Talent loss—especially of top engineers and vCIOs—is the fastest way for a post-sale integration MSP to leak the acquired enterprise valuation. Mitigate this flight risk by treating retention as a targeted effort, not a company-wide initiative.
Identify “deal-critical” roles by function, not title. This list includes L3 escalation owners, security leads, PSA/RMM administrators, and tribal knowledge holders responsible for the top 10 accounts.
For these individuals, structure a specific retention package anchored directly to integration outcomes. Incentives must be milestone-based, tied both to stay-through dates (e.g., 90 and 180 days) and verifiable cutover completions (platform migration finalized, billing integration complete).
Critically, anchor non-cash value. Provide a written role charter defining “what changes/what doesn’t” and immediate clarity on their new promotion path. Offering ownership of the future tech stack creates necessary long-term buy-in. Communicate this clarity within the first two weeks to shield the acquired asset from destructive ambiguity.
3. Proactively Manage Client Churn Risk and Define the Continuity Narrative
Integration failures surface when high-value clients discover operational changes through service friction (e.g., missed SLAs, new ticket portals). Mitigating this proactively is critical, as recurring revenue stability directly shields the acquired enterprise valuation.
Begin with rapid client segmentation by churn risk. Tier accounts by revenue, compliance burden, and bespoke workflow complexity (change sensitivity). Assign a senior owner to every top-tier account; this person serves as the “single throat to choke” for communication.
Prioritize continuity in all communication. Before announcing tooling updates, confirm what is stable: support hours, escalation paths, and security posture. Frame changes as “strengthening the engine,” assuring clients that commitment to uptime is unchanged.
Install formal feedback loops immediately. Schedule brief, outcome-focused check-ins using a simple “integration pulse” question (quality up/down, and why). This tracks client sentiment, enabling immediate intervention before service friction leads to cancellation.
4. Implement Delivery Guardrails: Separate ‘Run’ from ‘Change’
During a complex post-sale integration MSP, the chief risk is the cannibalization of operational resources. Pulling key staff from the Service Desk (“Run”) for integration (“Change”) causes immediate MTTR spikes and margin leakage.
Establish rigid operational guardrails. Dedicate an integration “tiger team” solely to the cutover plan, protecting the core helpdesk from distraction. Enforce freeze windows for high-risk changes (RMM agent swaps, PSA cutovers), ensuring these never occur during peak demand. Critically, define dedicated escalation coverage for the helpdesk while the tiger team operates.
Define success via weekly service KPIs: ticket backlog, MTTR, and SLA attainment. Set strict degradation thresholds; if surpassed, pause consolidation work immediately. Finally, document clear exception handling for critical client project requests that fall within the integration window. This subordinates consolidation to client uptime and sustained enterprise valuation. (139 words)
5. Define the Target Tech Stack and Data Authority
Vague technology integration plans are where technical debt is silently accrued, eroding future synergy realization and lowering your ultimate enterprise valuation. Avoid the common trap of protracted, low-velocity integrations by making two binary decisions now:
The Consolidation Decision
Commit to one path for major platforms (PSA, RMM, Documentation) and document the rationale:
- Option A: Temporary Bridging: Use light integrations to reduce immediate client disruption (minimal short-term risk). This only delays core consolidation; document the mandatory exit date.
- Option B: Full Migration: Immediately cut over to the superior platform standard (high short-term risk, maximum long-term efficiency). This is typically the superior path for PE-backed entities targeting aggressive growth and M&A readiness.
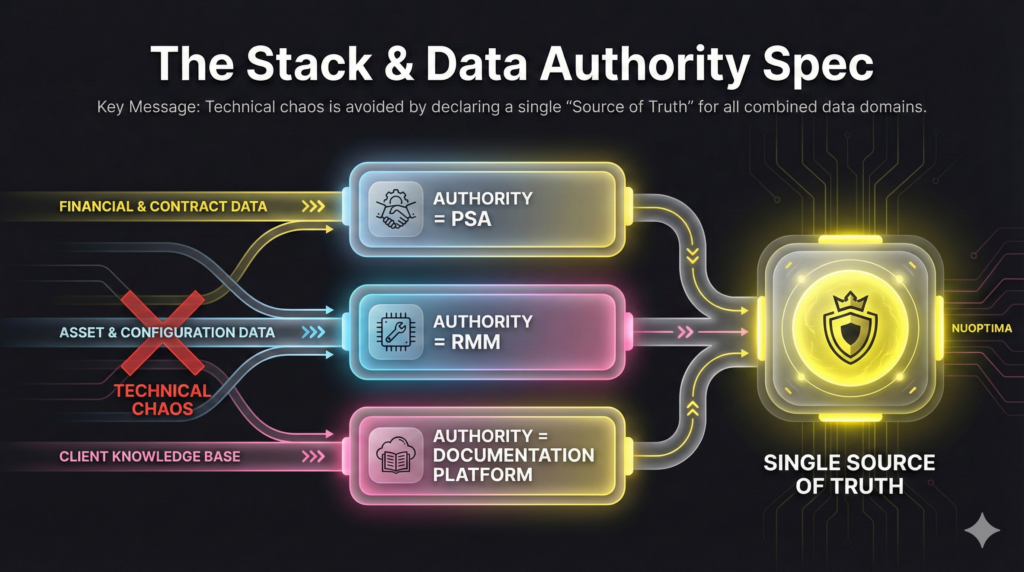
Declare the Source of Truth
Technical chaos ensues when data lives in two places. For every domain, declare the canonical “source of truth” system. This prevents duplicates and ensures data integrity:
- Financial/Contract Data: PSA
- Asset/Config Data: RMM
- Client Knowledge Base: Documentation Platform
Formalize these decisions in a 1-page “Stack & Data Authority” spec. This document is a critical asset for your IMO, guaranteeing the entire post-sale integration MSP team follows the same field ownership rules. (149 words)
6. Map Business Logic and Run Phased Validation
Executing a seamless post-sale integration MSP requires cataloging operational dependencies. Start by building a Migration Risk Register.
Build the Risk Register
Before migration, inventory custom logic that drives revenue and labor reduction:
- Automation Inventory: All custom scripts, workflow rules, and PSA triggers.
- Configuration Mapping: Custom fields (EDF), configuration naming standards, and client-specific access rules.
- Integration Dependencies: Backup systems, SOC/SIEM feeds, and artifact-generating systems (e.g., historical billing data).
This process identifies known failure modes (broken automation, duplicate configurations) for prioritized validation testing.
Run a Phased Rollout and Pilot
Mitigate risks using a rigorous pilot program. Select a low-risk client cohort (5–10 clients) to validate the end-to-end delivery flow: alert → ticket → dispatch → resolution → accurate billing.
Initiate the phased rollout only after full validation. Migrate in waves, holding until stability thresholds (normalized ticket volume, confirmed automation coverage) are met. Post-cutover, measure hard outcomes: ticket volume shifts and technician time reclaimed (time-to-efficiency). (141 words)
7. Run a Compliance Delta Assessment to Standardize Controls
Inheriting hidden, non-compliant client obligations erodes M&A value. Your initial three weeks must include a rigorous compliance delta assessment. This assessment identifies the mismatch in the acquired MSP’s documented controls, client contractual obligations (for regulated sectors like Healthcare or Finance), and your target regulatory frameworks (CMMC, HIPAA, SOC 2).
Identify specific tool coverage gaps: Is EDR coverage adequate? Does backup meet immutability standards? Highest risk is the acquired entity serving regulated clients with controls weaker than contracts demand.
Immediately standardize to a single, defensible policy baseline and exception process. Align incident response, logging/retention, and vendor management procedures. Communicate these mandatory control changes transparently to clients: what changes, timelines, and how the combined entity will provide auditable evidence collection going forward. (138 words)
8. Normalize Billing Mechanics and Establish Centralized Financial Reporting
Margin leakage is the silent killer of acquired enterprise valuation. Misaligned contracts and pricing models cause the combined MSP to underbill while leadership focuses on technical integration.
Immediately unify billing rules. Normalize critical elements: pricing units (per user, per device), inclusion/exclusion standards, and project rate cards. Resolve the “what’s bundled” ambiguity fast, especially regarding managed security, backup, and M365 licensing. Failure guarantees the delivery of unbilled services.
Standardize financial reporting immediately. Track transition costs (training, migration partners) against realized savings (consolidated licenses) to prove synergy realization. Establish a mandatory monthly margin leakage review to isolate unbilled time, contract mismatches, tool overlap, and discount creep. This produces one combined KPI pack leadership can trust for long-term EBITDA stability.
9. Establish a Unified KPI Spine for M&A Readiness
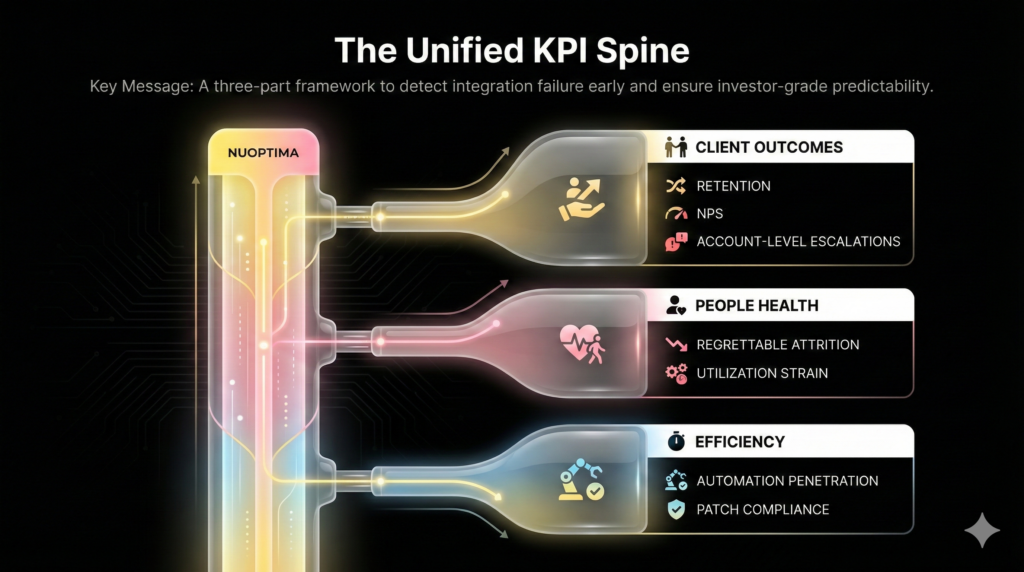
Protecting the acquired enterprise valuation requires a unified KPI spine that meets investor scrutiny, especially when preparing for a future private equity exit, and ensures long-term predictability. Implement this critical 3-part measurement framework immediately to detect integration failure early:
- Client Outcomes: Focus on retention via churn risk segmentation and NPS/CSAT movement. Track escalations per account and SLA attainment within the first 90 days post-platform integration. Stable recurring revenue is the clearest signal of successful post-sale integration MSP delivery.
- People & Delivery Health: Protect gross margin by monitoring regrettable attrition, especially among L3 staff and security leads. Track utilization strain (after-hours load). Core operational metrics include Ticket Backlog, First-Contact Resolution (FCR), and normalized MTTR.
- Efficiency & Controls: Measure automation coverage penetration and patch compliance adherence—hard proof of operational maturity.
Set an aggressive weekly review cadence for 90 days, then shift to monthly. Crucially, tie every action item to a functional owner, ensuring this data rigor drives tangible EBITDA outcomes.
The 100-Day Execution Schedule for Post-Sale MSP Integration
Converting an M&A playbook into realized enterprise value requires a rigorous operational schedule that subordinates all technical work to client continuity. This 100-day schedule is an execution mandate. Ensure you tackle governance, people, and revenue protection in the correct sequence before initiating high-risk platform migration.
Days 0–14: Stabilize and Establish Control (Governance & Risk Triage)
Use the first two weeks to establish high-velocity governance and mitigate immediate flight risks among staff and high-value clients. Do not attempt optimization or migration yet.
- Stand up the IMO structure, formally appoint the Integration Lead, and publish decision rights for all functional owners (Item 1).
- Identify and engage all deal-critical staff (L3s, Security Leads). Deliver retention conversations anchored to written role charters (Item 2).
- Segment all clients by churn risk. Launch the continuity narrative and executive communication plan for your top revenue tier (Item 3).
- Publish service guardrails and the capacity plan. Enforce a project freeze on the Service Desk, formally separating the integration “Change” team from the client-facing “Run” team (Item 4).
- Outcome: Governance fully operational; highest people/client risks mitigated; core service delivery protected from integration shock.
Days 15–45: Decide the Stack and Prove the Path with a Pilot
Declare the target state for technology and validate the migration strategy before execution begins.
- Declare the Stack and Data Authority. Commit to the superior platform for PSA, RMM, and Documentation. Declare the canonical source of truth for core asset, financial, and configuration data (Item 5).
- Build the Migration Risk Register, mapping all acquired automation and custom fields. Execute the end-to-end pilot with a small, low-risk client group to prove the new delivery flow (Item 6).
- Run the Compliance Delta Assessment (Item 7). Identify major gaps and set interim standardized controls immediately for all regulated clients to reduce audit exposure.
- Outcome: Target state systems defined; migration logic tested; regulatory exposure quantified.
Days 46–75: Execute Waves, Protect SLAs, and Fix Billing Reality
Execute mass migration after the pilot completion. Rigorously protect service performance and eliminate financial leakage.
- Run phased migrations in batches, adhering strictly to the thresholds established in the service guardrails. Pause consolidation work if Service KPIs (MTTR, backlog) breach defined limits (Items 4 + 6).
- Normalize contracts and pricing (Item 8). Unify rate cards and resolve all scope ambiguity surrounding bundled security and licensing to eliminate silent margin leakage.
- Expand client communication beyond Tier 1. Shift the messaging to “what improved” reporting, demonstrating realized stability (Item 3).
- Outcome: Core data migrated; billing standardized; realized margin improvement validated.
Days 76–100: Standardize, Document, and Lock the New Operating Model
Secure realized synergies, shift the company to business-as-usual, and prepare the acquired asset for long-term M&A readiness.
- Move the IMO cadence from weekly firefighting to a monthly executive review. Update all standard operating procedures (SOPs), onboarding checklists, and internal ownership maps.
- Run the final KPI review (Item 9). Quantify service stability, staff retention, consolidation progress, and the improved unit economics (EBITDA lift).
- Conduct a post-mortem review of the integration process: document what worked, what to change, and what automation must be built before the next roll-up event.
- Outcome: New operating model stabilized; efficiencies quantified; documentation complete; M&A readiness secured.
FAQ
Integration planning must begin during the due diligence phase, prior to close. This involves defining the target operating model, the governance structure (IMO), and the resources required. Execution—including platform cutovers and staff realignment—only begins post-close under the agreed-upon access constraints. Define your first 30-day priorities, such as service guardrails and immediate client communication narratives, before Day 1.
Base the decision on client risk profile and organizational integration capacity. Running tools in parallel (temporary bridging) reduces immediate client disruption but creates tool sprawl and reporting inconsistency, which must be sunsetted by a firm deadline. Full migration is riskier short-term but delivers immediate efficiency and is generally the superior path for maximizing long-term enterprise valuation. (See Item 5 for the consolidation decision breakdown.)
Reduce uncertainty by providing role clarity and defining clear escalation paths within the first two weeks. For deal-critical talent, structure milestone-based retention offers tied to successful integration outcomes (e.g., 90-day and 180-day completion dates). Offering ownership of the future unified tech stack also provides valuable non-cash buy-in and a clear promotional path, mitigating flight risk.
Assume yes. All acquired custom logic, including workflow rules, custom scripts, and PSA/RMM custom fields, must be inventoried in a Migration Risk Register (see Item 6). These automations are critical business logic; they must be explicitly mapped and validated using a rigorous pilot program before rolling out the full migration to protect SLA and billing integrity.
Prioritize proactive communication and stability over immediate optimization. Assign a named senior owner to every high-value client to manage the relationship. Frame all technical changes (new ticket portals, tool swaps) as “strengthening the security posture” and “improving reporting.” Show visible, positive outcomes immediately, such as enhanced security monitoring or faster response times, to reinforce the continuity narrative.